Configure SSO between Azure AD and Samsung Knox
Configuring SSO in Knox
- Login to Samsung Knox
- In the top-right hand corner, click your Avatar icon, then select Account Information
- On the left-hand side click SSO Settings
- Browse to the Azure Active Directory Portal
- In the left-hand pane, click Azure Active Directory, then click Enterprise Applications
- Click New Application
- Enter Samsung Knox and Business Services into the search box


- Click the app, then click Create
- Once created, click Users and group
- Click Add user/group, then click None Selected under Users and Groups to add your assignment.
I recommend using a dedicated Azure AD group for Samsung Knox Administrators
- Once you have selected your user/group, click Assign
- Click Single sign-on in the left-hand pane
- Click SAML
- Configure the following Basic SAML Configuration settings, then click Save
- Identifier (Entity ID): Leave default (https://www.samsungknox.com)
- Reply URL: https://central.samsungknox.com/ams/ad/saml/acs
- Sign on URL: https://accounts.samsung.com/
- Copy the contents of the App Federation Metadata Url under SAML Signing Certificate
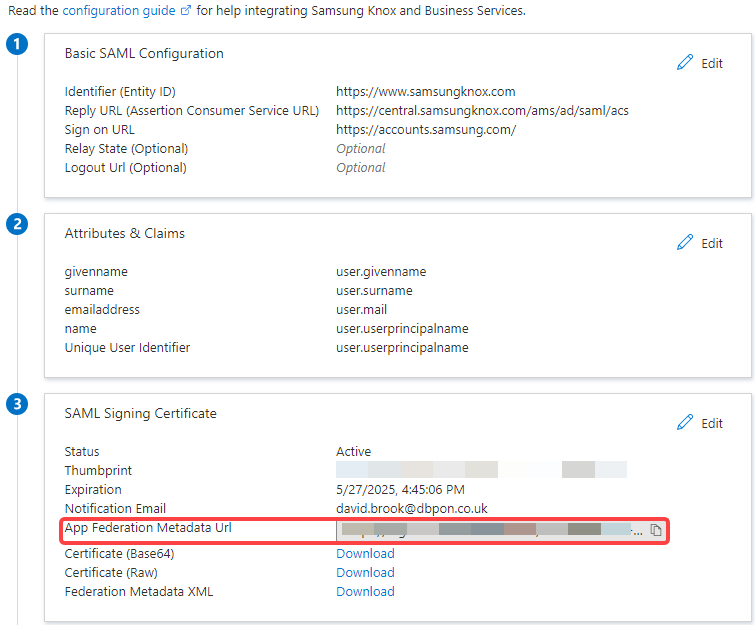

- Navigate back to the SSO Settings page in Samsung Knox
- Paste the copied contents into the App federation metadata URL box
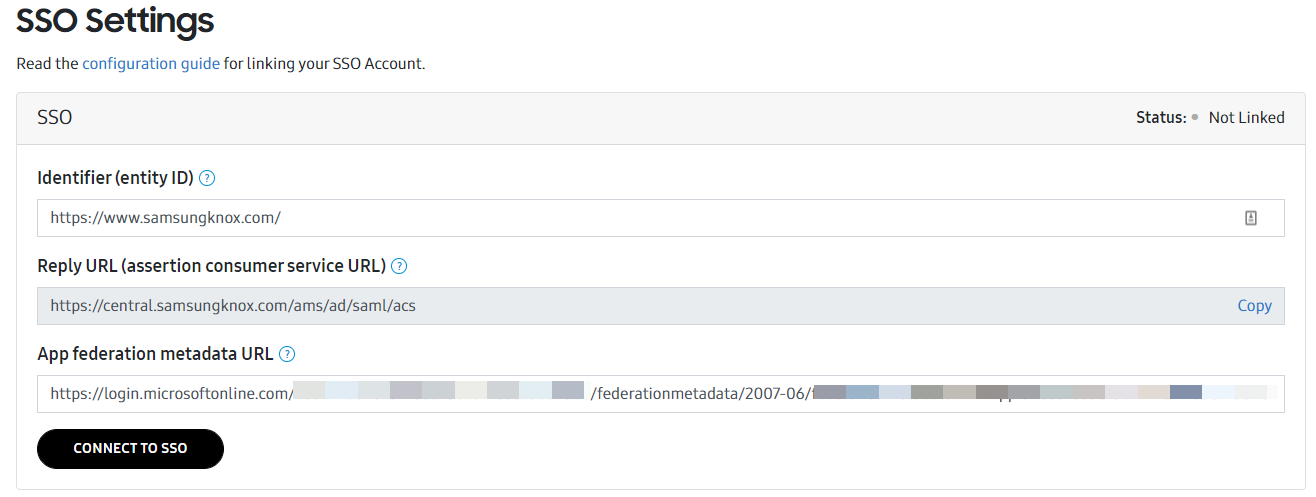

- Click Connect to SSO
- Sign in with your AAD Credential
The user you initially configure SSO with must be the Super Admin Account. Ensure the user was selected or is within a selected group in steps 10/11.
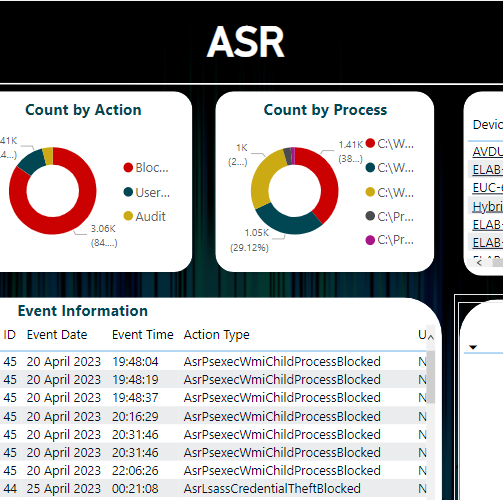
Things to be aware of
- If your account already has permissions to another Knox Suite, you will not be able to use your account
- Once you configure SSO for Knox, you can not use a mixture of Samsung and SSO Accounts, you can only use SSO Accounts.
- The App on the My Apps will not sign you into Knox
- Any account that has already been configured will continue to work with their SSO Credentials providing they are in scope of enterprise app
- To add a user to Knox, you are still required to send the invite in the first instance from Knox, Adding them to the scope does not suffice
- If when you sign-in you receive a Sorry, you don’t have access screen, ensure that a Samsung Knox administrator within your organization has configured an account for you.
Conclusion
Using SSO for applications such as Knox will save admins time and effort storing multiple password and identities.
I tried numerous ways to configure the application to open the Knox portal from the MyApps page to no avail. If you have managed to succeed in doing so, I would love to hear from you :).
Categories
Tags
Configure SSO between Azure AD and Samsung Knox
Configuring SSO in Knox
- Login to Samsung Knox
- In the top-right hand corner, click your Avatar icon, then select Account Information
- On the left-hand side click SSO Settings
- Browse to the Azure Active Directory Portal
- In the left-hand pane, click Azure Active Directory, then click Enterprise Applications
- Click New Application
- Enter Samsung Knox and Business Services into the search box


- Click the app, then click Create
- Once created, click Users and group
- Click Add user/group, then click None Selected under Users and Groups to add your assignment.
I recommend using a dedicated Azure AD group for Samsung Knox Administrators
- Once you have selected your user/group, click Assign
- Click Single sign-on in the left-hand pane
- Click SAML
- Configure the following Basic SAML Configuration settings, then click Save
- Identifier (Entity ID): Leave default (https://www.samsungknox.com)
- Reply URL: https://central.samsungknox.com/ams/ad/saml/acs
- Sign on URL: https://accounts.samsung.com/
- Copy the contents of the App Federation Metadata Url under SAML Signing Certificate


- Navigate back to the SSO Settings page in Samsung Knox
- Paste the copied contents into the App federation metadata URL box


- Click Connect to SSO
- Sign in with your AAD Credential
The user you initially configure SSO with must be the Super Admin Account. Ensure the user was selected or is within a selected group in steps 10/11.
Things to be aware of
- If your account already has permissions to another Knox Suite, you will not be able to use your account
- Once you configure SSO for Knox, you can not use a mixture of Samsung and SSO Accounts, you can only use SSO Accounts.
- The App on the My Apps will not sign you into Knox
- Any account that has already been configured will continue to work with their SSO Credentials providing they are in scope of enterprise app
- To add a user to Knox, you are still required to send the invite in the first instance from Knox, Adding them to the scope does not suffice
- If when you sign-in you receive a Sorry, you don’t have access screen, ensure that a Samsung Knox administrator within your organization has configured an account for you.
Conclusion
Using SSO for applications such as Knox will save admins time and effort storing multiple password and identities.
I tried numerous ways to configure the application to open the Knox portal from the MyApps page to no avail. If you have managed to succeed in doing so, I would love to hear from you :).