Deny Resource Type Creation with Azure Policy
What is Azure Policy?
Azure Policy is a way to help organisations enforce standards and compliance. Azure Policy is commonly used for things like enforcing only certain allowed locations for resources, locating non-compliant Azure resources and for many, many other reasons.
For a full overview of Azure Policy, please take a look at the Microsoft Documentation.
Why would you want to deny resource creation?
There could be many reasons, such as wanting to prevent the creation of Virtual Machines, Network Security Groups, Storage Accounts, to name a few. A requirement I came up against recently was a client wanted to prevent the creation of New Virtual Machines inside a subscription.
What is the Solution?
The solution to the problem is to create an Azure Policy definition and assign it to your Management Group, Subscription or to a specific resource group.
You can assign a Policy Definition more than once, it can also be assigned at different levels each time.
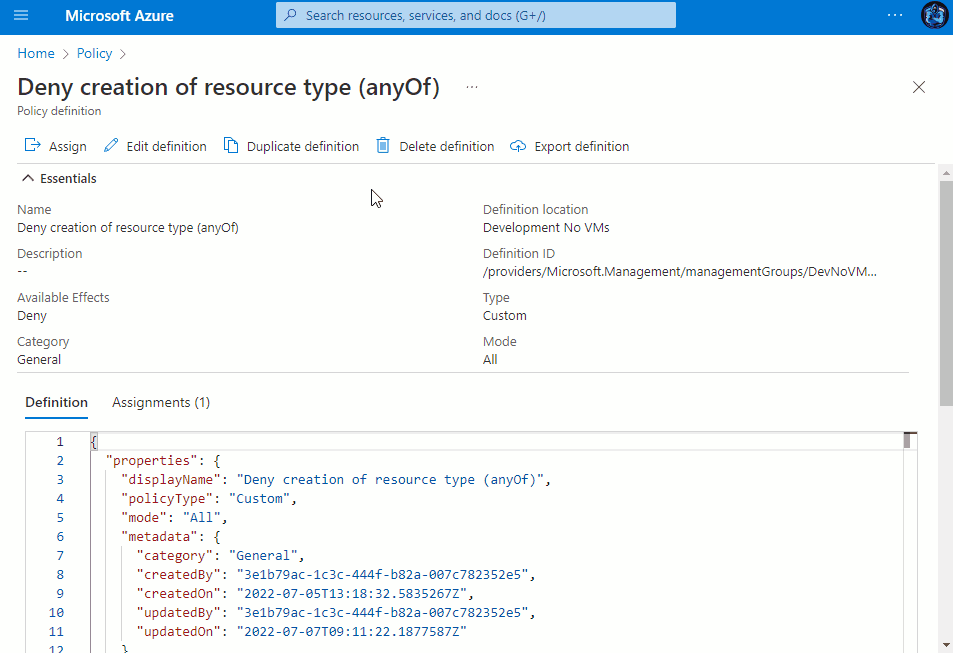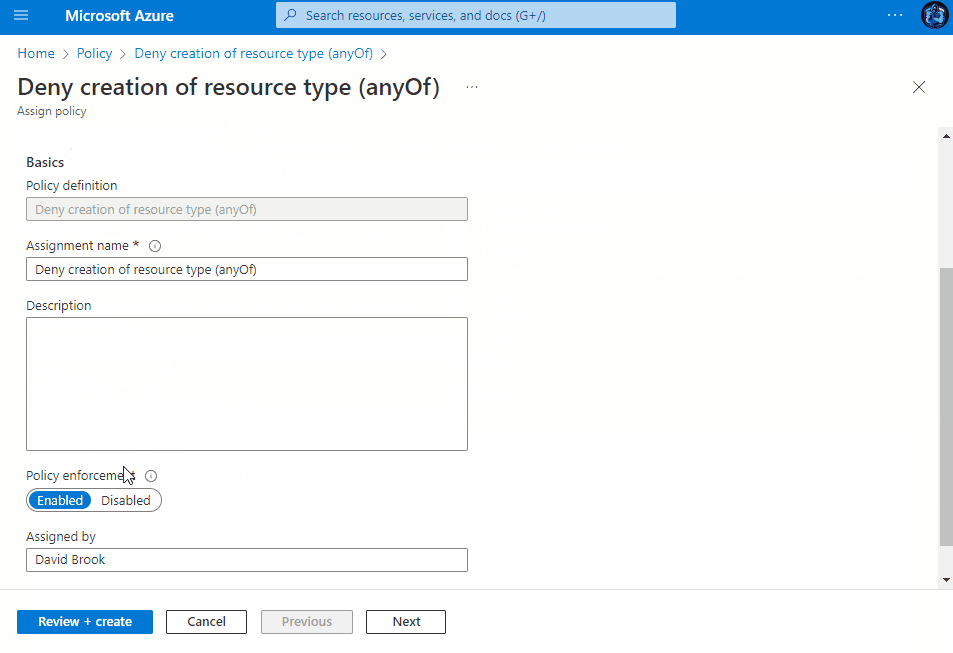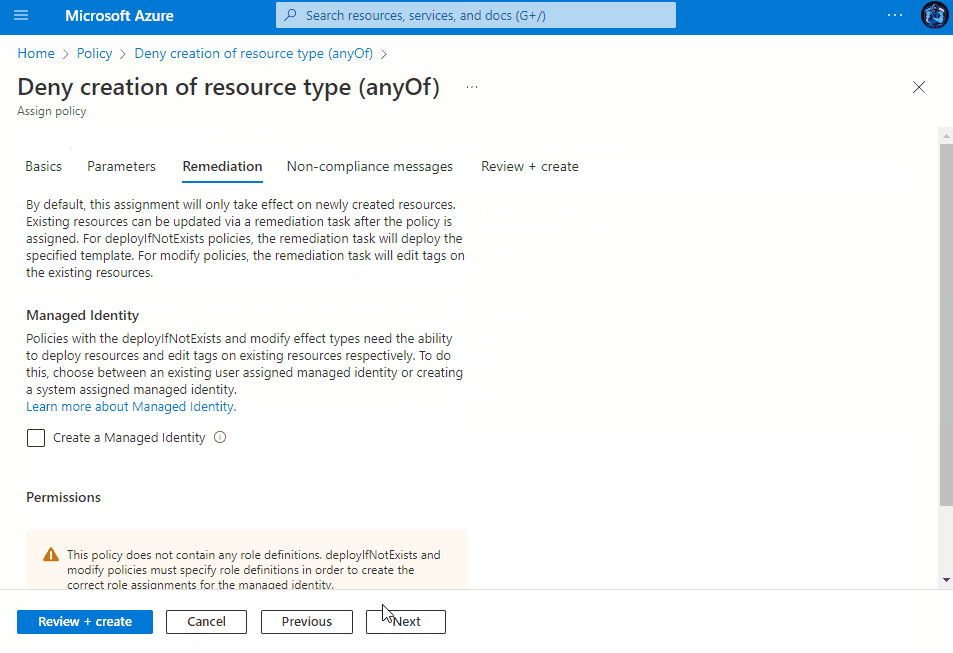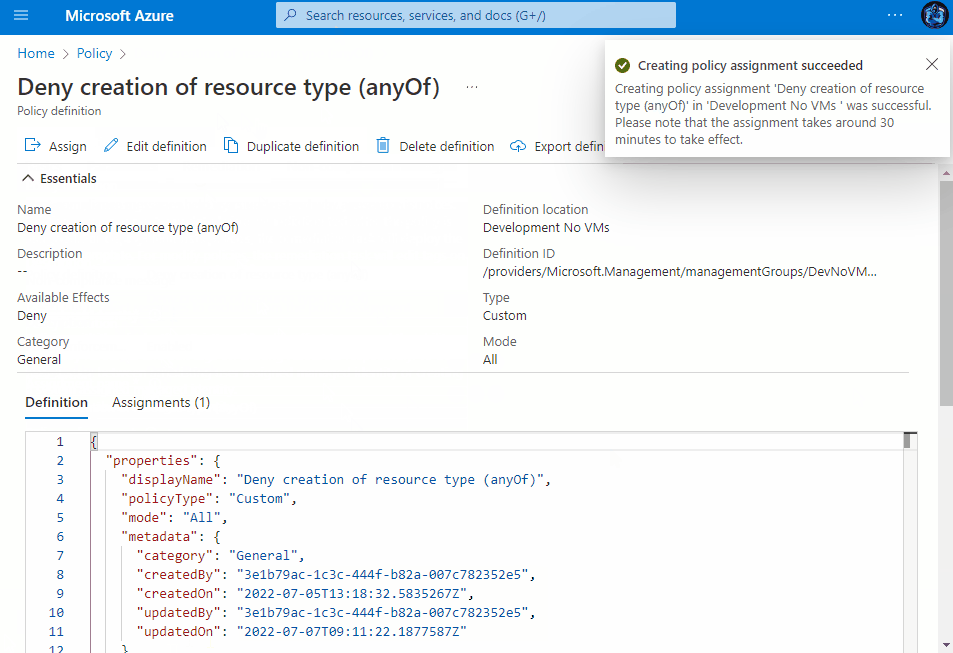
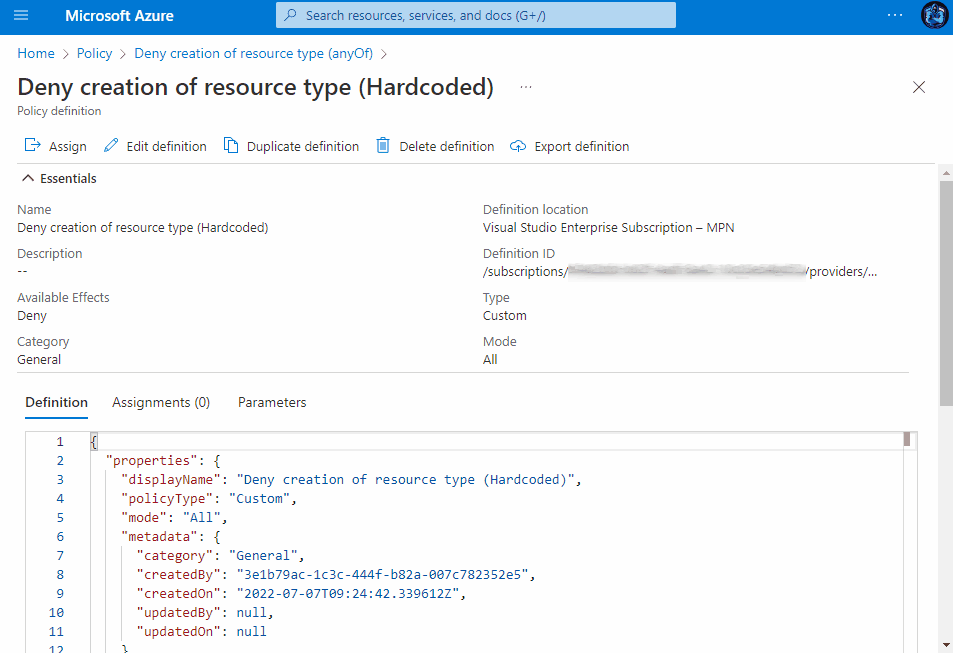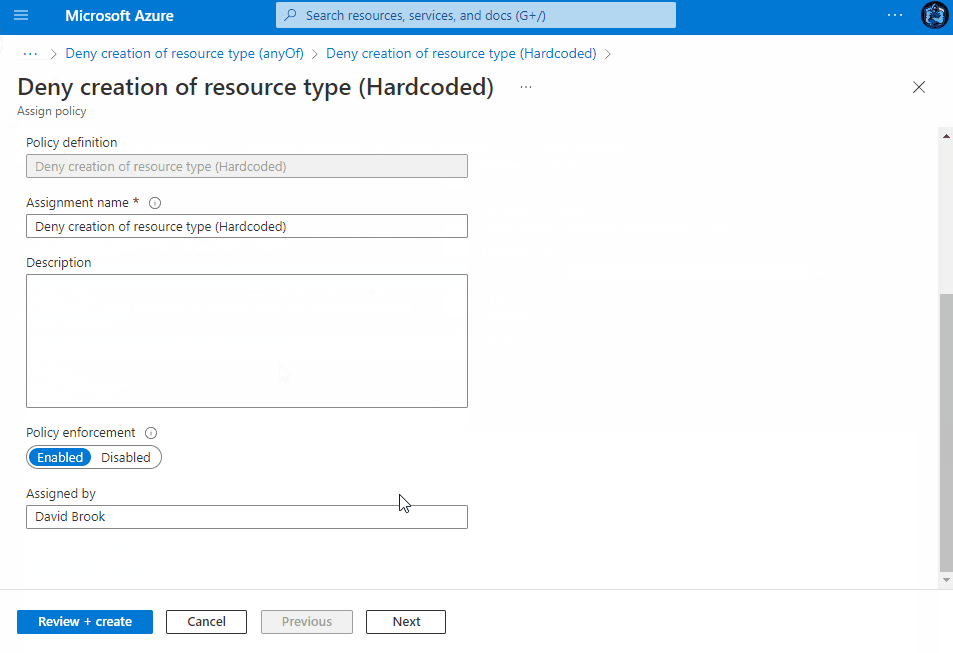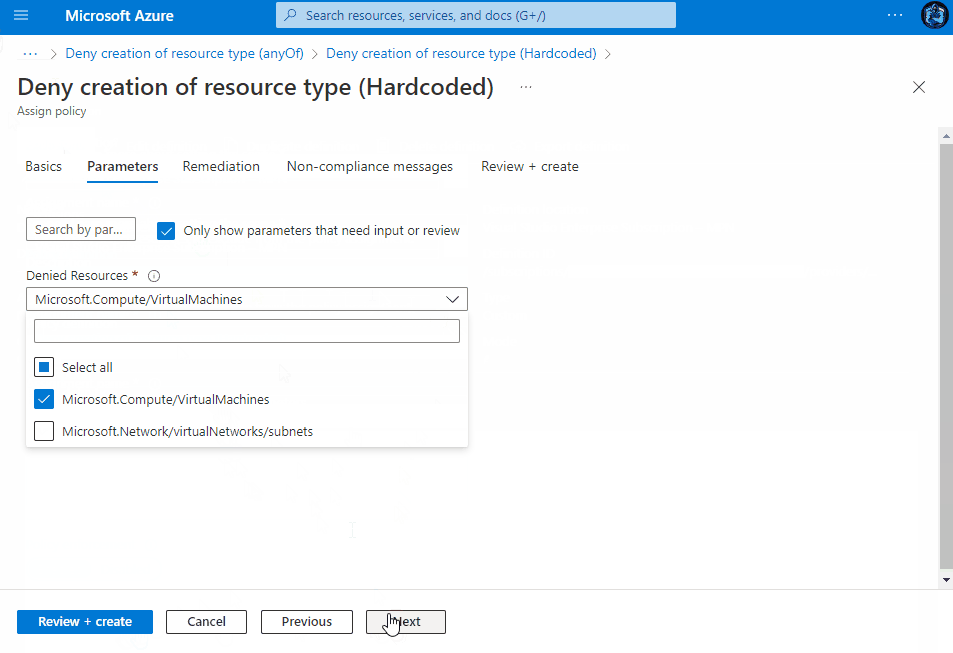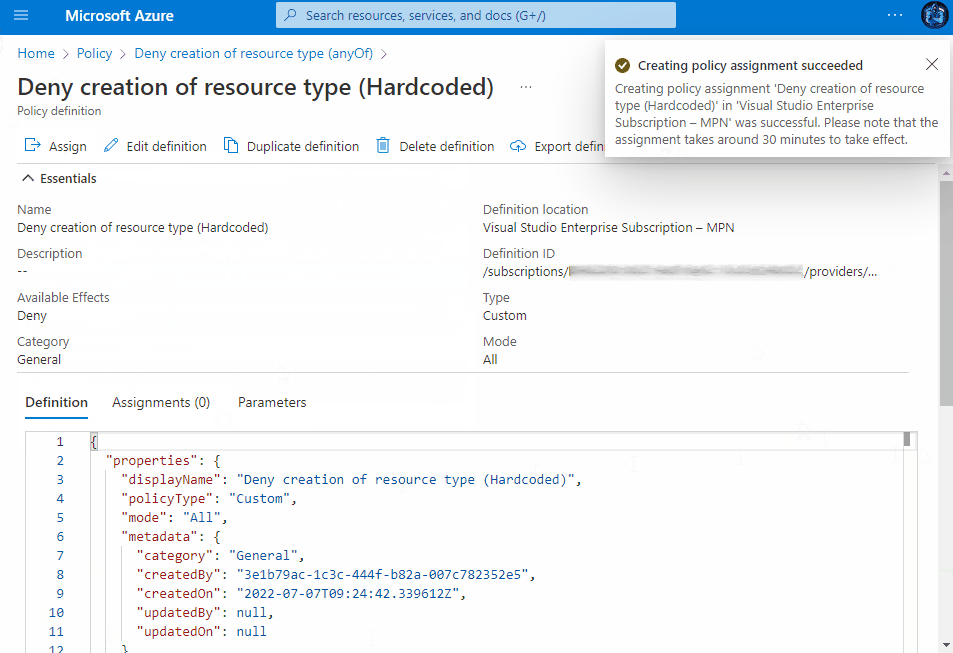
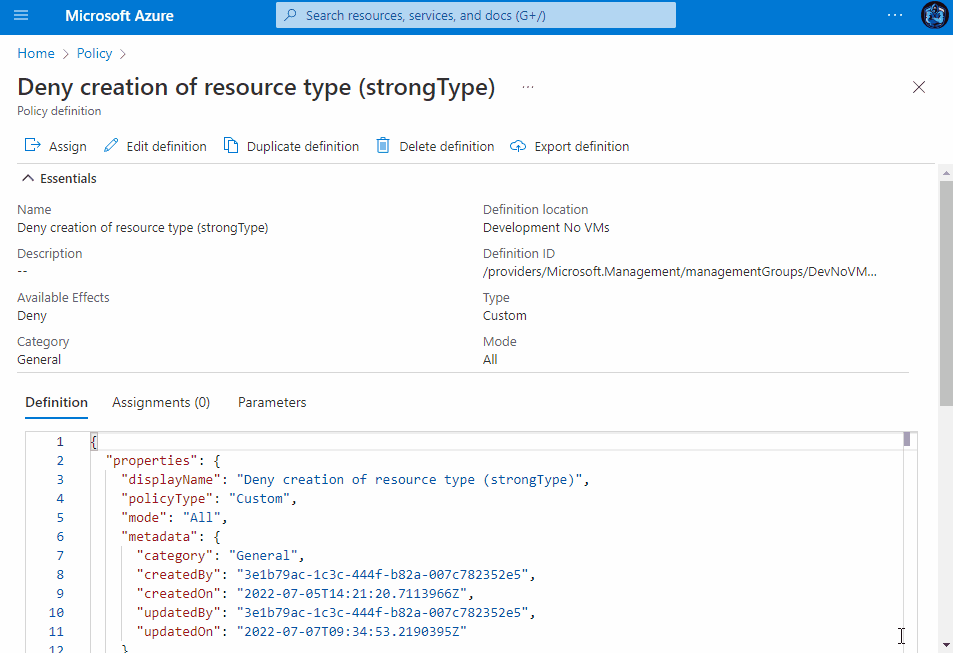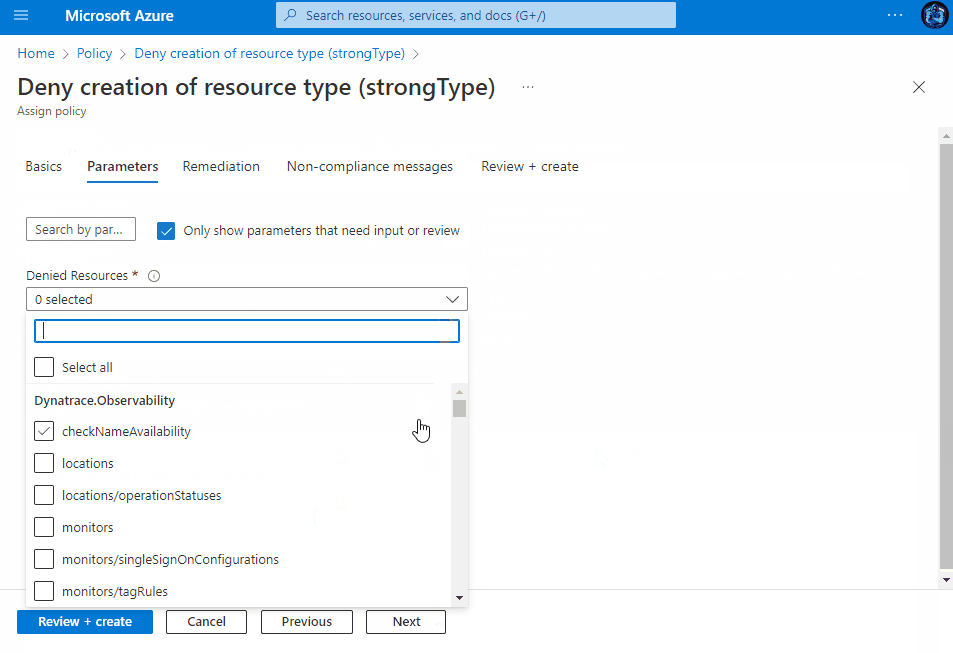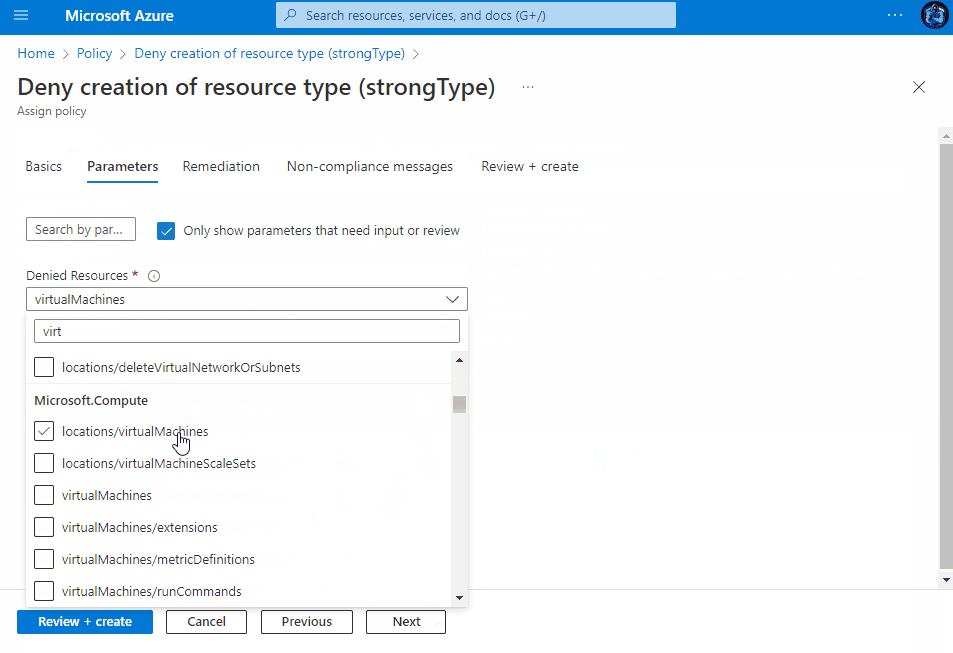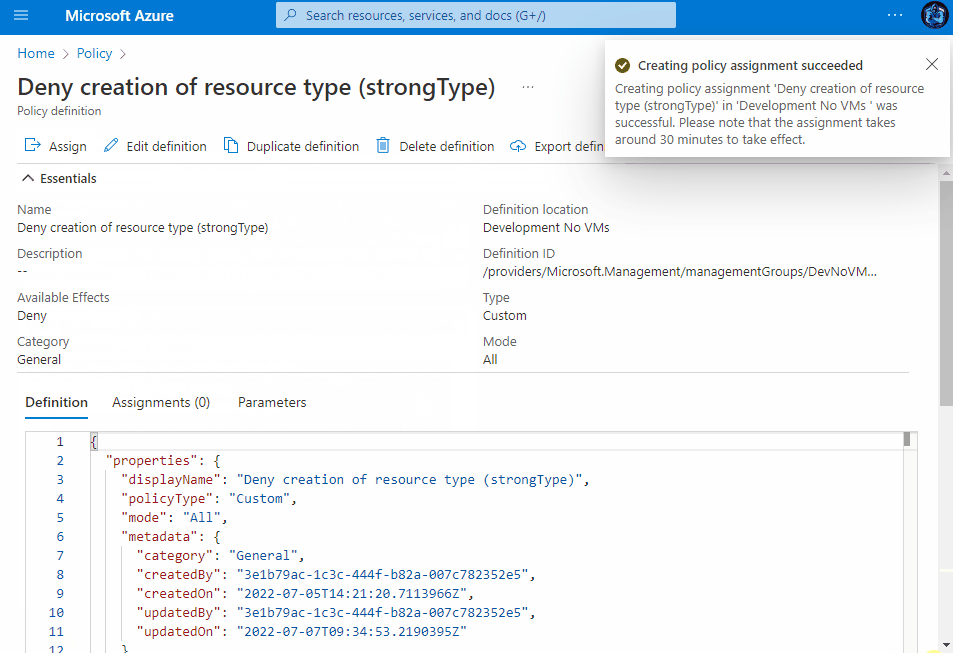
There are various ways you can create the definition, for example, you can hardcore your parameters, you can make use of Azure strongTypes and have a drop down menu to select your resource types or you can simply apply them in an anyOf array, see the different definition snippets, along with their assignment experiences in the drop-downs below.
Create an Azure Policy Definition
- Browse to the Azure Portal
- Use the search bar and locate Policy
- Select Definitions from the left-hand pane
- Click + Policy definition
- Enter the following details;
- Select your desired definition location
- Enter a descriptive name
- Add a description
- Select or Create a new category for your definition to live within
- Copy and paste your desired definition snippet from one of the above drop-downs.
- Click Save
Assigning the Policy
Once saved, you then have the ability to assign the Policy to a Subscription, Management Group or a Resource group within a subscription. You can view the assignment experience within the drop-downs above to see how it behaves depending on your chosen method.
Conclusion
The route I would take would be to use the strongType list and name the definition something along the lines of <COMPANY SHORTCODE>-Deny Resource Types. This will allow you to use a single definition to define which resources to deny in different Subscriptions, Management Groups or Resource Groups.
Resouces
Categories
Tags
Deny Resource Type Creation with Azure Policy
What is Azure Policy?
Azure Policy is a way to help organisations enforce standards and compliance. Azure Policy is commonly used for things like enforcing only certain allowed locations for resources, locating non-compliant Azure resources and for many, many other reasons.
For a full overview of Azure Policy, please take a look at the Microsoft Documentation.
Why would you want to deny resource creation?
There could be many reasons, such as wanting to prevent the creation of Virtual Machines, Network Security Groups, Storage Accounts, to name a few. A requirement I came up against recently was a client wanted to prevent the creation of New Virtual Machines inside a subscription.
What is the Solution?
The solution to the problem is to create an Azure Policy definition and assign it to your Management Group, Subscription or to a specific resource group.
You can assign a Policy Definition more than once, it can also be assigned at different levels each time.
There are various ways you can create the definition, for example, you can hardcore your parameters, you can make use of Azure strongTypes and have a drop down menu to select your resource types or you can simply apply them in an anyOf array, see the different definition snippets, along with their assignment experiences in the drop-downs below.
Create an Azure Policy Definition
- Browse to the Azure Portal
- Use the search bar and locate Policy
- Select Definitions from the left-hand pane
- Click + Policy definition
- Enter the following details;
- Select your desired definition location
- Enter a descriptive name
- Add a description
- Select or Create a new category for your definition to live within
- Copy and paste your desired definition snippet from one of the above drop-downs.
- Click Save
Assigning the Policy
Once saved, you then have the ability to assign the Policy to a Subscription, Management Group or a Resource group within a subscription. You can view the assignment experience within the drop-downs above to see how it behaves depending on your chosen method.
Conclusion
The route I would take would be to use the strongType list and name the definition something along the lines of <COMPANY SHORTCODE>-Deny Resource Types. This will allow you to use a single definition to define which resources to deny in different Subscriptions, Management Groups or Resource Groups.