Import GPOs to Group Policy Analytics using Graph API
Many organisations are starting to adopt cloud technologies, some of which decide to start again with a clean slate and add in policies where necessary. However, some organisations still look to take migrate their complex Group Policies.
Your content goes here.I would recommend taking the approach of clean slate, aligned to relevant framework(s) such as NCSC, NIST or CIS and applying only relevant policies there after.
CIS: CIS Critical Security Controls Cloud Companion Guide (cisecurity.org)
NCSC: Windows – NCSC.GOV.UK
This post is to aid any IT Administrator in achieving goals, weather that be to analyse your current policies or only a selection of polices. There will be a script to export the Group Policies from a specific OU, and a script to recursively import the XML files to Intune utilising the Graph API.
The scripts detailed in this post are available on GitHub.
Getting Started
Permissions
Intune
One of the following permissions is required to use Group Policy Analytics.
- Intune Administrator
- Any role that includes the Security Baseline permission
Group Policy
- This article assumes the Administrator has access to read and export the GPOs within the targeted scope.
- The export script will need to be run on an endpoint with Group Policy Management Tools Installed
Running the Script(s)
All scripts will need to be run with the Execution Policy of the PowerShell terminal set to bypass. If preferred, scripts can be launched prefixed with the below;
`powershell.exe -exectutionpolicy Bypass -File`
Export Group Policies
This script is used to export Group Policy Objects using PowerShell. When executing the script you will need to specify which OU ( `-OU ` ) you want to export the policies from and also the folder ( `-GPOFolder` ) where you want the exports to be stored.
The script is extensible, so if you want to widen the scope or make amendments, make it work for you.
If you execute the script with a command like below, you will see the policy GUIDs that are exported as displayed in the clip.
`“.Get-LinkedGPOs.ps1” -OU “OU=Managed_Devices,DC=Domain,DC=LAB” -GPOFolder “$env:SystemDriveTempGPOs”`


Importing Group Policies to Group Policy Analytics
Importing the policy exports to Group Policy Analytics is just as simple as exporting them with the use of the `Import-GroupPolicyAnalyticsPolicy.ps1` script. This script was designed for a specific purpose, to save time and clicks!.
For this example, we will start by taking a look at some of the parameters that are used upon launch.
- GPOFolder (Mandatory): This parameter is to be used to point the script to your .XML files.
- Recurse: If you have group policies nested inside other folders, this parameter is advised to recursively import them.
- LogOutputLocation: A location for the created logfile output, default is C:Temp.
- TenantID: If you are calling this script for any other tenant, other than the one you have previously logged into, you will need to specify the TenantID.
- UseDeviceAuthentication: Offers the ability to use Device Authentication.
This script will only import Group Policies with Unique names, it does a check on the names prior to import.
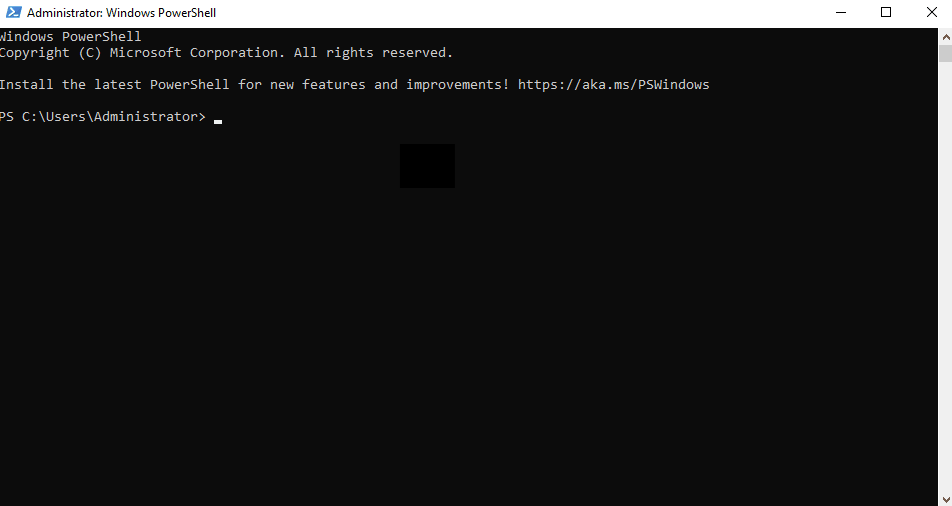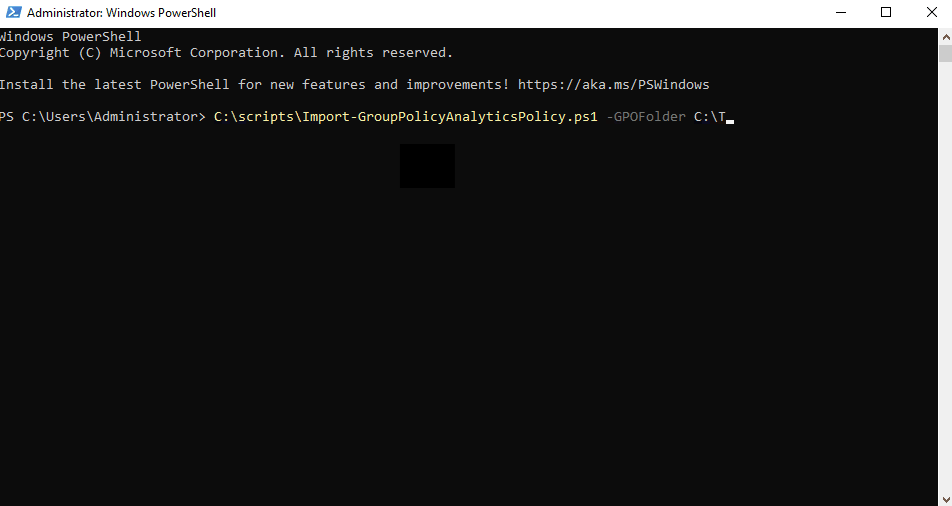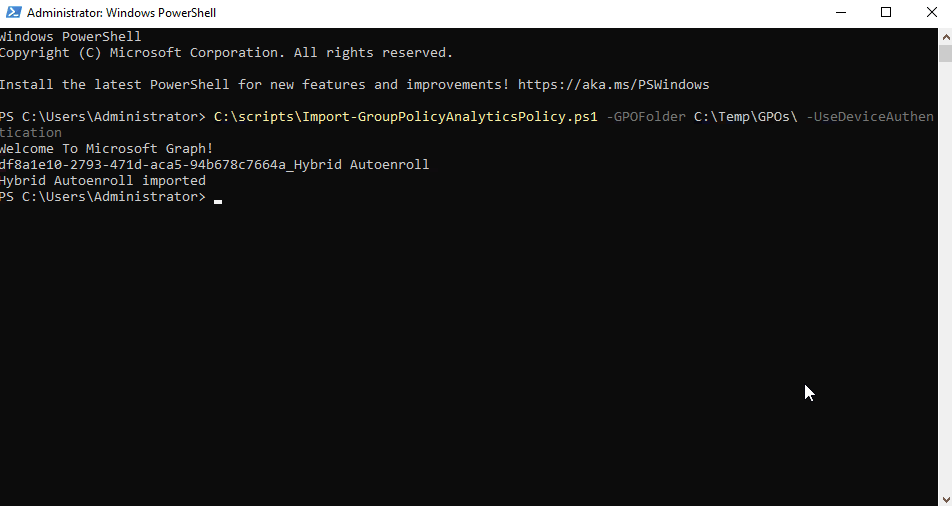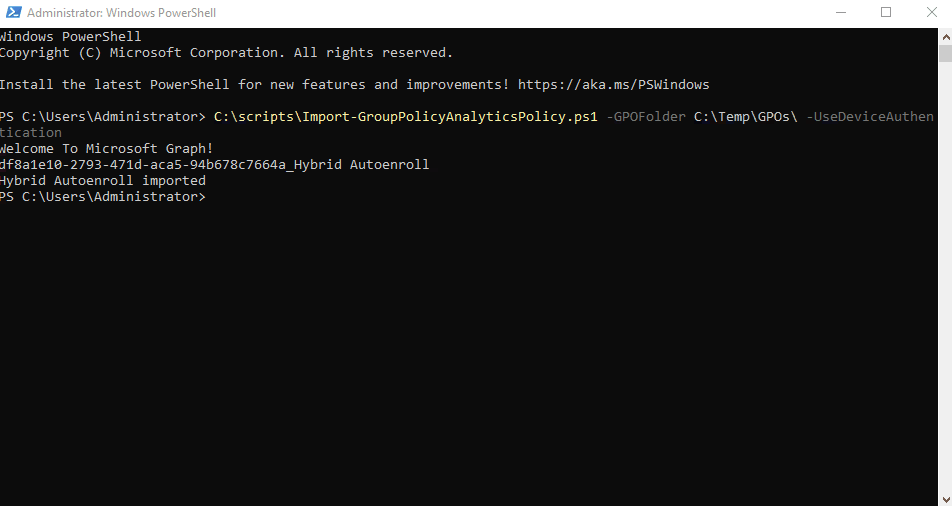
Once you are ready, you can execute the script with the relevant parameters, for example you can run the following command to import the policies.
`“Import-GroupPolicyAnalyticsPolicy.ps1.ps1” -GPOFolder “$env:SystemDriveTempGPOs” -UseDeviceAuthentication`

Results
This results in the Group Policy being available within Intune, as below;

Conclusion
This was a quite good to pull together, I hope you can put it to good use and make your life a lot easier and less pain staking.
Please leave feedback and comments below if you would like to see more things like this.
Further Reading
For further reading on Group Policy Analytics, please review the Microsoft Documentation.
Categories
Tags
Import GPOs to Group Policy Analytics using Graph API
Many organisations are starting to adopt cloud technologies, some of which decide to start again with a clean slate and add in policies where necessary. However, some organisations still look to take migrate their complex Group Policies.
Your content goes here.I would recommend taking the approach of clean slate, aligned to relevant framework(s) such as NCSC, NIST or CIS and applying only relevant policies there after.
CIS: CIS Critical Security Controls Cloud Companion Guide (cisecurity.org)
NCSC: Windows – NCSC.GOV.UK
This post is to aid any IT Administrator in achieving goals, weather that be to analyse your current policies or only a selection of polices. There will be a script to export the Group Policies from a specific OU, and a script to recursively import the XML files to Intune utilising the Graph API.
The scripts detailed in this post are available on GitHub.
Getting Started
Permissions
Intune
One of the following permissions is required to use Group Policy Analytics.
- Intune Administrator
- Any role that includes the Security Baseline permission
Group Policy
- This article assumes the Administrator has access to read and export the GPOs within the targeted scope.
- The export script will need to be run on an endpoint with Group Policy Management Tools Installed
Running the Script(s)
All scripts will need to be run with the Execution Policy of the PowerShell terminal set to bypass. If preferred, scripts can be launched prefixed with the below;
`powershell.exe -exectutionpolicy Bypass -File`
Export Group Policies
This script is used to export Group Policy Objects using PowerShell. When executing the script you will need to specify which OU ( `-OU ` ) you want to export the policies from and also the folder ( `-GPOFolder` ) where you want the exports to be stored.
The script is extensible, so if you want to widen the scope or make amendments, make it work for you.
If you execute the script with a command like below, you will see the policy GUIDs that are exported as displayed in the clip.
`“.Get-LinkedGPOs.ps1” -OU “OU=Managed_Devices,DC=Domain,DC=LAB” -GPOFolder “$env:SystemDriveTempGPOs”`


Importing Group Policies to Group Policy Analytics
Importing the policy exports to Group Policy Analytics is just as simple as exporting them with the use of the `Import-GroupPolicyAnalyticsPolicy.ps1` script. This script was designed for a specific purpose, to save time and clicks!.
For this example, we will start by taking a look at some of the parameters that are used upon launch.
- GPOFolder (Mandatory): This parameter is to be used to point the script to your .XML files.
- Recurse: If you have group policies nested inside other folders, this parameter is advised to recursively import them.
- LogOutputLocation: A location for the created logfile output, default is C:Temp.
- TenantID: If you are calling this script for any other tenant, other than the one you have previously logged into, you will need to specify the TenantID.
- UseDeviceAuthentication: Offers the ability to use Device Authentication.
This script will only import Group Policies with Unique names, it does a check on the names prior to import.
Once you are ready, you can execute the script with the relevant parameters, for example you can run the following command to import the policies.
`“Import-GroupPolicyAnalyticsPolicy.ps1.ps1” -GPOFolder “$env:SystemDriveTempGPOs” -UseDeviceAuthentication`


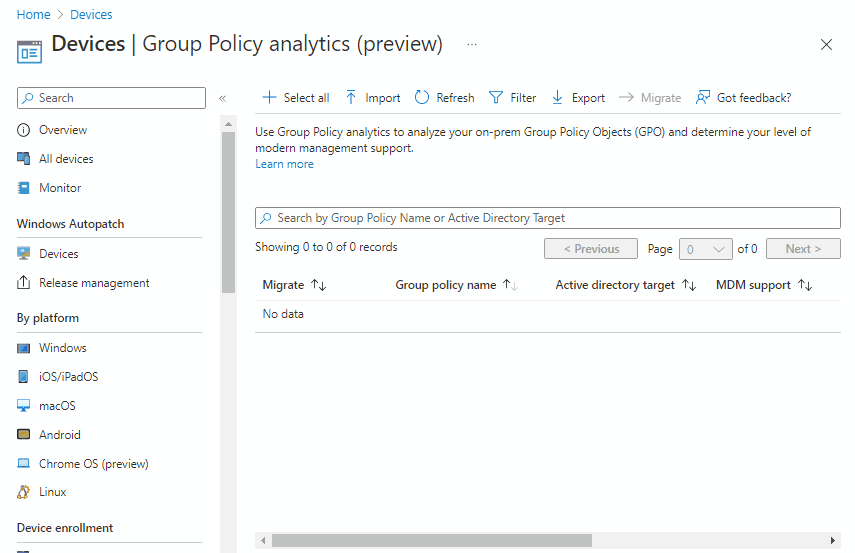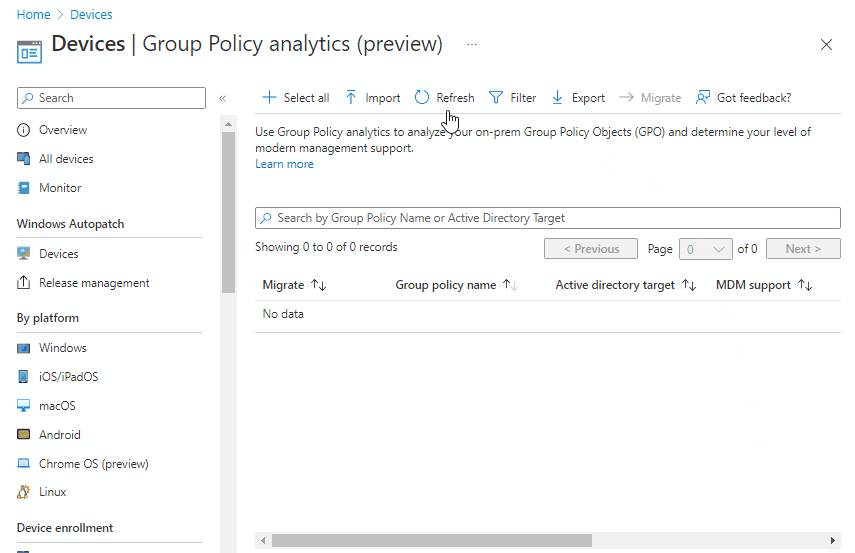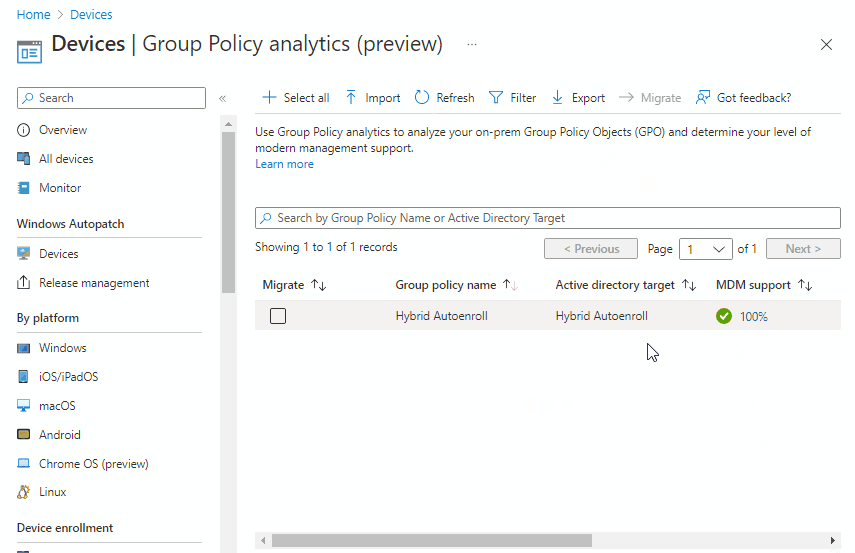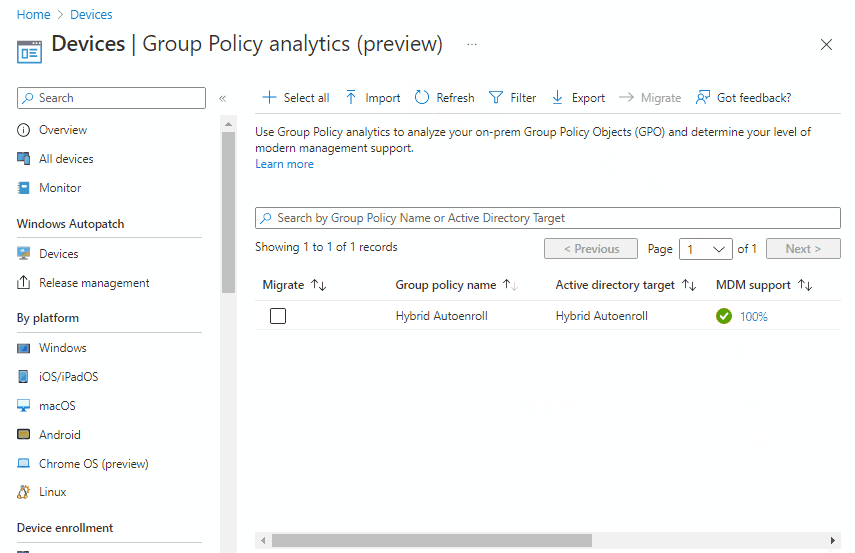
Results
This results in the Group Policy being available within Intune, as below;


Conclusion
This was a quite good to pull together, I hope you can put it to good use and make your life a lot easier and less pain staking.
Please leave feedback and comments below if you would like to see more things like this.
Further Reading
For further reading on Group Policy Analytics, please review the Microsoft Documentation.