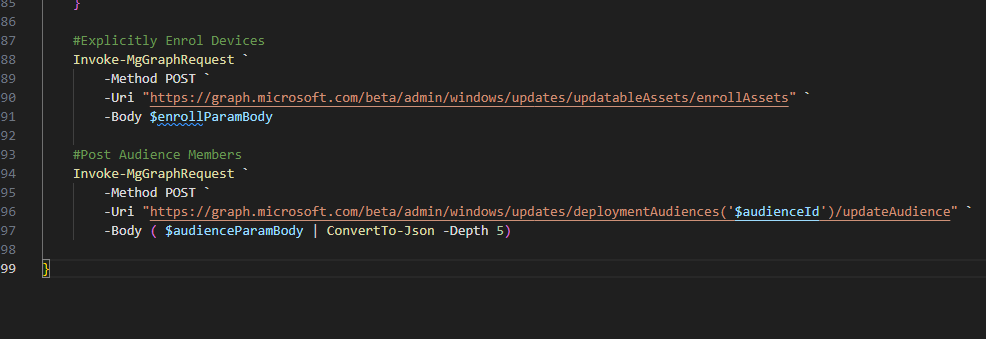
Add Offer Deferrals to Driver and Firmware Policies
It’s been a day or so since the release of the public preview of Driver and Firmware management (SEE PRESS RELEASE HERE), and many of you may have used the GUI to create your policies, and have been left scratching your head as to why you cannot specify a deferral period. Well, let me let you into a secret, IT IS.
If you have looked at my Driver Management via Graph API and PowerShell post, I call it out within the Create an Update Policy section.
So, how do we add this to our policies so you don’t have to re-create your policies? Let’s take a look shall we.
Prerequisites
- Permissions to connect to the Graph API with the following scopes
- WindowsUpdates.ReadWrite.All
- Microsoft.Graph PowerShell Module
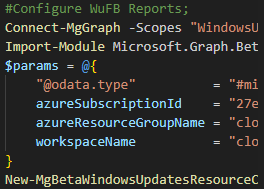
Connecting to the Graph API
Connecting via this module could not be easier, follow the below steps after ensuring the Microsoft.Graph module is installed.;
- Launch a PowerShell prompt
- Enter `Connect-MgGraph -Scopes WindowsUpdates.ReadWrite.All -ContextScope Process`, hit Enter
- Sign in, If not already consented, you will be prompted with an image like the below. You can choose to grant for yourself or your organisation if you have the permissions.
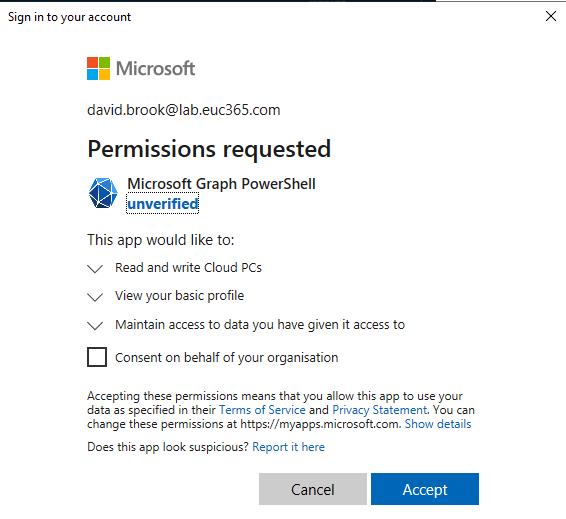

Microsoft Graph Profile Selection
The first thing we need to do before running any commands is call `Select-MgProfile -Name beta` to ensure we are using the Beta endpoint of the Microsoft Graph.
Add/Update Deferral Dates
Throughout the rest of this article we will be referring to a script called Update-PatchDeferrals.ps1, this script can be found by using the GitHub Resource link below.
The aim of this script is to simplify the process as much as possible for everyone. I will step through the manual process so the understanding of what is happening is there, but for simplicity, the use of the script (or function within) will be the better option.
To update a policy using the script, it simply needs to be called as follows;
`Update-PatchDeferrals.ps1 -updatePolicyID ‘cc4fbe71-a024-41c2-a99f-559dcde6e916’ -deferralTime ‘PT5D’`
Looking through the Function
The basic premise of this script is to use the current complianceChangeRules, but only modify the durationBeforeDeploymentStart property which will control the deferral date. I thought the simplest way to do this was to pull in the current configuration, and amend only the durationBeforeDeploymentStart property. Let’s take a look at how we achieve this then shall we.
First of all, we have our Mandatory parameters, updatePolicyID and the deferralTime. The update policy ID can be found by looking at the Listing Update Policies section in my original article.
The deferralTime, is the parameter that gives us what we need. This needs to be formatted in the ISO8601 standards for duration (LINK), for example, If we added PT1H, that would defer the update for an hour before offering. If we was to use P10D, that would defer the offer for 10 days.
The first thing the function then does in the begin section is form the base object for the POST request later in the module, it then fulfils the `$complianceChangeRules` variable with the current settings from the policy.
In the process section, this is where the object combines the `$paramBody` and the `$complianceChangeRules` objects, and then for each object in the complianceChangeRules array, it will update the deferral time.
Finally, within the end section, we post the `$paramBody` object to the Graph API to update the deferral on the policy.
This deferral will only apply to updates approved Automatically after the change has been made. Any current approvals are unaffected.
Closing Thoughts
From what I have been seeing in the community, there seems to be an air of expectation that this would have been released with Intune UI Capability. However, what has been released is the foundations of the building, it is everything that underpins the structural walls of what is to come!, without what we have today, the roof would never be added!
Categories
Tags
Add Offer Deferrals to Driver and Firmware Policies
It’s been a day or so since the release of the public preview of Driver and Firmware management (SEE PRESS RELEASE HERE), and many of you may have used the GUI to create your policies, and have been left scratching your head as to why you cannot specify a deferral period. Well, let me let you into a secret, IT IS.
If you have looked at my Driver Management via Graph API and PowerShell post, I call it out within the Create an Update Policy section.
So, how do we add this to our policies so you don’t have to re-create your policies? Let’s take a look shall we.
Prerequisites
- Permissions to connect to the Graph API with the following scopes
- WindowsUpdates.ReadWrite.All
- Microsoft.Graph PowerShell Module
Connecting to the Graph API
Connecting via this module could not be easier, follow the below steps after ensuring the Microsoft.Graph module is installed.;
- Launch a PowerShell prompt
- Enter `Connect-MgGraph -Scopes WindowsUpdates.ReadWrite.All -ContextScope Process`, hit Enter
- Sign in, If not already consented, you will be prompted with an image like the below. You can choose to grant for yourself or your organisation if you have the permissions.


Microsoft Graph Profile Selection
The first thing we need to do before running any commands is call `Select-MgProfile -Name beta` to ensure we are using the Beta endpoint of the Microsoft Graph.
Add/Update Deferral Dates
Throughout the rest of this article we will be referring to a script called Update-PatchDeferrals.ps1, this script can be found by using the GitHub Resource link below.
The aim of this script is to simplify the process as much as possible for everyone. I will step through the manual process so the understanding of what is happening is there, but for simplicity, the use of the script (or function within) will be the better option.
To update a policy using the script, it simply needs to be called as follows;
`Update-PatchDeferrals.ps1 -updatePolicyID ‘cc4fbe71-a024-41c2-a99f-559dcde6e916’ -deferralTime ‘PT5D’`
Looking through the Function
The basic premise of this script is to use the current complianceChangeRules, but only modify the durationBeforeDeploymentStart property which will control the deferral date. I thought the simplest way to do this was to pull in the current configuration, and amend only the durationBeforeDeploymentStart property. Let’s take a look at how we achieve this then shall we.
First of all, we have our Mandatory parameters, updatePolicyID and the deferralTime. The update policy ID can be found by looking at the Listing Update Policies section in my original article.
The deferralTime, is the parameter that gives us what we need. This needs to be formatted in the ISO8601 standards for duration (LINK), for example, If we added PT1H, that would defer the update for an hour before offering. If we was to use P10D, that would defer the offer for 10 days.
The first thing the function then does in the begin section is form the base object for the POST request later in the module, it then fulfils the `$complianceChangeRules` variable with the current settings from the policy.
In the process section, this is where the object combines the `$paramBody` and the `$complianceChangeRules` objects, and then for each object in the complianceChangeRules array, it will update the deferral time.
Finally, within the end section, we post the `$paramBody` object to the Graph API to update the deferral on the policy.
This deferral will only apply to updates approved Automatically after the change has been made. Any current approvals are unaffected.
Closing Thoughts
From what I have been seeing in the community, there seems to be an air of expectation that this would have been released with Intune UI Capability. However, what has been released is the foundations of the building, it is everything that underpins the structural walls of what is to come!, without what we have today, the roof would never be added!